Why Should I Care About OAuth 2.0?
As an application developer, you may have heard the term OAuth 2.0 thrown around a lot. OAuth 2.0 has gained wide adoption by web service and software companies around the world and is integral to the way these companies interact and share information. But what exactly is it? In a nutshell.
OAuth 2.0 is a protocol that allows distinct parties to share information and resources in a secure and reliable manner
Note
What about OAuth 1.0?
Built with the same motivation, OAuth 1.0 was designed and ratified in 2007. However, it was criticized for being overly complex and also had issues with imprecise specifications, which led to insecure implementations. All of these issues contributed to poor adoption for OAuth 1.0, and eventually led to the design and creation of OAuth 2.0. OAuth 2.0 is the successor to OAuth 1.0.
It is also important to note that OAuth 2.0 is not backward compatible with OAuth 1.0, and so OAuth 2.0 applications cannot integrate with OAuth 1.0 service providers.
What problems does it solve?
Have you ever logged into a site using your Google account? Have you ever posted to Pinterest and Instagram at the same time? Have you ever shared a link to your wall from any application other than Facebook? These are all examples of OAuth 2.0 in use!
At a high level, the OAuth 2.0 protocol allows two parties to exchange information securely and reliably. In more practical terms, you'll find that the most common uses of OAuth 2.0 involve two things:
- Allowing a user to log into an application with another account. For example, Pinterest allows users to log in with their Twitter accounts. This is known as federated identity.
- Allowing one service to access resources on another service on behalf of the user. For example, Adobe accessing your Facebook photos on your behalf. This is known as delegated authority.
How does OAuth 2.0 actually solve the problem?
In order to see how OAuth 2.0 solves this problem of sharing resources, let's look at how this problem was solved before OAuth 2.0 was created.
Without OAuth 2.0 – StudyLink App wants to suggest contacts by looking at your Facebook friends
Imagine that you have just signed up for the service StudyLink App. As a new user, you don't have any contacts. StudyLink App wants to suggest contacts for you to add by looking at your Facebook friends. If any of your Facebook friends are on StudyLink App, it will suggest that you add them.
Before the creation of OAuth 2.0, this was solved in a very insecure way. StudyLink App would ask you for your username and password for Facebook. StudyLink App would then log into Facebook on your behalf to get your friends. This interaction can be looked at like this:
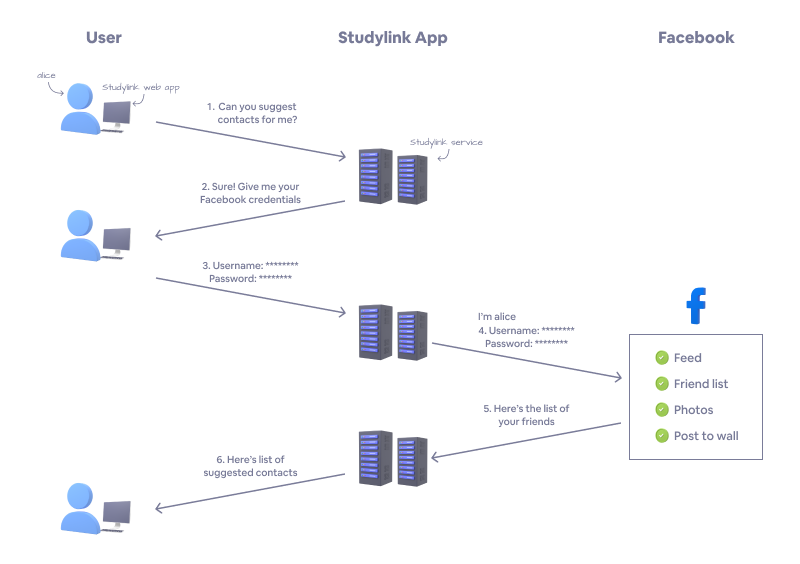
Here is how it works:
- You ask StudyLink App to suggest contacts to you.
- StudyLink App responds by saying, "Sure! Just give me your Facebook username and password please!"
- You give StudyLink App your username and password for your Facebook account.
- StudyLink App then logs into Facebook using your credentials, effectively impersonating you, to request your friend list.
- Facebook happily obliges, giving StudyLink App your friend list.
- StudyLink App then uses this information to tailor suggested contacts for you.
Why is this a bad idea? There are five key reasons:
- You have given StudyLink App the power to do *anything* with your account: This is known proverbially as giving it the "keys to the city". You have essentially given StudyLink App access to everything in your account as if they were you. Now imagine it wasn't a StudyLink App. Instead, it was NewUnknownApp. It's easy to see how this becomes very dangerous.
- StudyLink App may save your password, and may do so insecurely: In order for StudyLink App to maintain access to your account, they would need to store your credentials. The act of storing your password is an extremely bad practice and should be avoided at all times. To make things worse, different companies enforce different standards of security, some of which are shockingly low.
- You are given more chances for your password to get stolen: You are sending your username and password across the Internet. The more times you do this, the more risk there is for someone to steal it.
- You have to change your Facebook password if StudyLink App ever gets hacked: If StudyLink App somehow got compromised, your Facebook credentials will also have been compromised. You would then need to change your Facebook password as a result of the StudyLink App getting owned.
- There is no way to revoke access: If StudyLink App was acquired by EvilCorp and started doing things that you didn't like, the only way to revoke access would be to change your Facebook credentials.
With OAuth 2.0 – StudyLink App wants to suggest contacts by looking at your Facebook friends
Now, let's take a look at that interaction, but this time utilizing the OAuth 2.0 protocol. In this scenario, StudyLink App would "ask" Facebook for your friend list. You give permission to this by logging into Facebook and approving the request. Once the request is approved, StudyLink App would then be able to fetch your friend list from Facebook on your behalf.
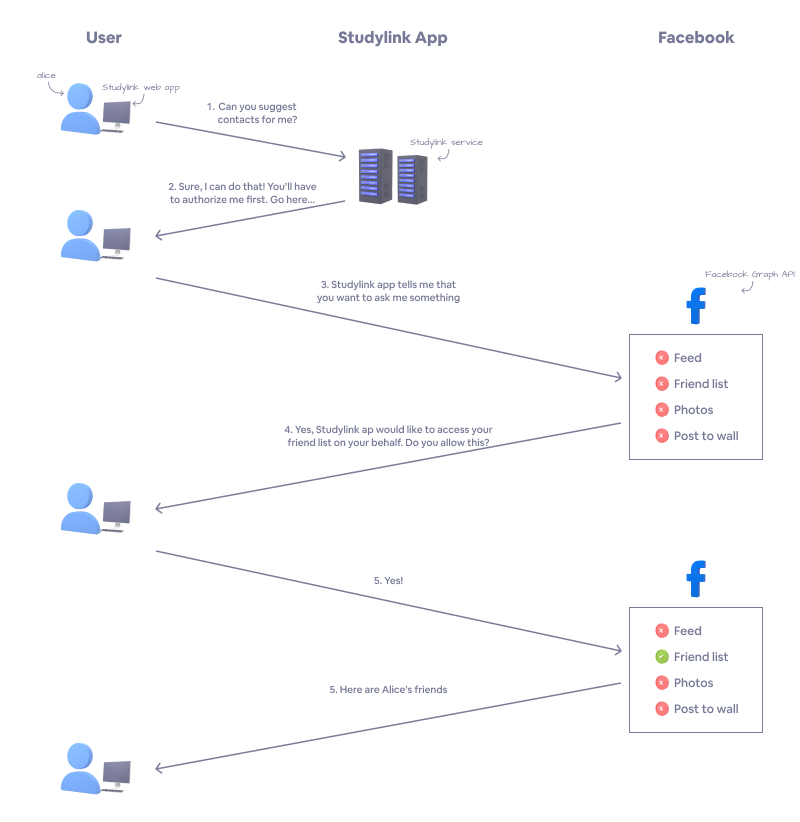
Let's have a look at the flow:
- You ask StudyLink App to suggest contacts to you.
- StudyLink App says, "Sure! But you'll have to authorize me first. Go here…"
- StudyLink App sends you to Facebook to log in and authorize StudyLink App.
- Facebook asks you directly for authorization to see if StudyLink App can access your friend list on your behalf.
- You say "yes".
- Facebook happily obliges, giving StudyLink App your friend list. StudyLink App then uses this information to tailor suggested contacts for you.
Why is this better? Five key reasons to contrast the five points in the previous example:
- You aren't giving it the "keys to the city" anymore: Notice, in this example, you aren't giving your Facebook username and password to StudyLink App. Instead, you are giving it directly to Facebook. Now, StudyLink App doesn't have to even worry about your Facebook credentials.
- Since you aren't giving your credentials, StudyLink App no longer needs to store them: With your authority delegated from Facebook, you don't need to worry that StudyLink App is storing, or even seeing, your Facebook password.
- You send your password across the Internet less frequently: If you already had an active session with Facebook, you actually wouldn't need to reauthenticate with them. If StudyLink App has federated identities with Facebook, you would have to send your password even less frequently.
- You don't have to change your Facebook password if StudyLink App ever gets hacked: This is because of the next point.
- There is a way to revoke access: OAuth 2.0 provides the ability for a service provider to revoke access to a client. If StudyLink App ever got compromised or got acquired by Evil Corp, you could go to Facebook and revoke StudyLink App's access.
Summary:
We took an introductory look at what OAuth 2.0 is and how it is used all around us. We discussed the benefits that this protocol gives us and even looked at the kind of adoption that has taken place in the industry. It has become one of the most, if not the most, used and adopted authorization protocols on the Internet due, in large part, to the power that it gives application developers, start-ups, and corporations alike, to share information.

Himanshu Thakkar
"LIVE as if you were to DIE tomorrow, LEARN as if you were to live forever..." Forever a student of technology. A programmer who fixes problems that you don’t know you have, in a way you don’t understand.